90% of data leakage is caused by user mistakes!
With a cleverly worded email and one unfortunate click, a hacker can gain access to your system within minutes, and stay there for an average of 286 days before being detected.
How can you avoid this scenario? Keep reading to learn about the three most common ways hackers can gain access to your system and the holistic approach Microsoft 365 takes to keep them out.
Cyber-attacks can happen any time, any day. Security threats are on the rise as criminals have built lucrative businesses from stealing data. No organisation is immune, and the numbers are sobering.
At illuminance Solutions our goal is to keep your business running without interruptions while remaining secure.
Key Attack Zone 1: Email
It takes hackers 4 minutes to get into networks through email attacks and
286 days for detection followed by an additional 80 days for damage control.

Open email from attacker.
286 days
Detect intrusion
80 days
Damage control

Will open attachment or link.
Key Attack Zone 2: User
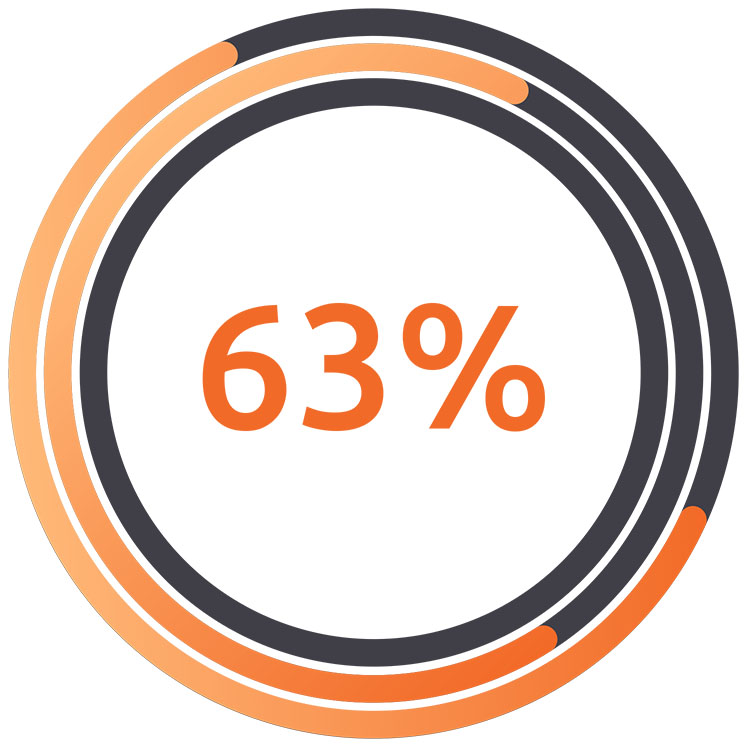
Weak, default or stolen passwords.
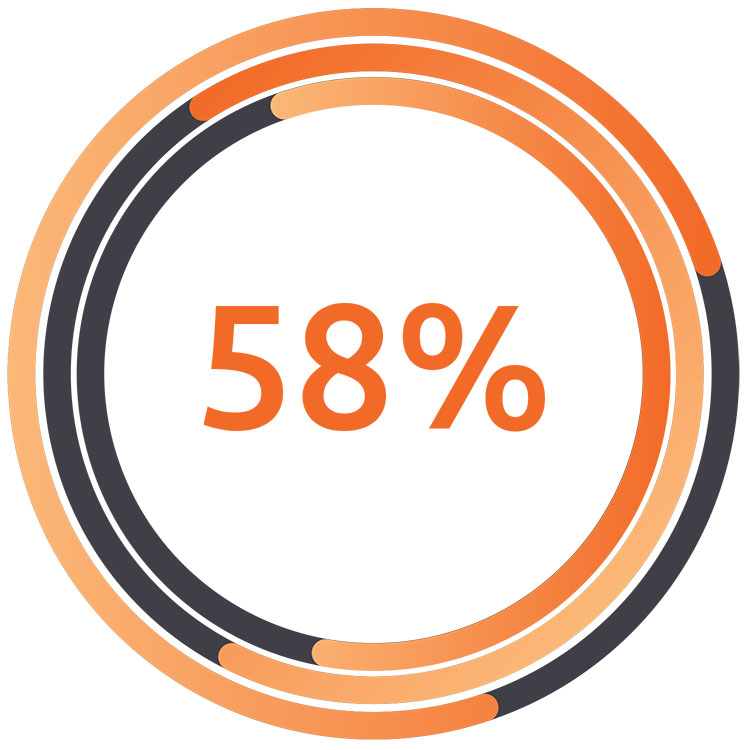
Accidentally share sensitive information.
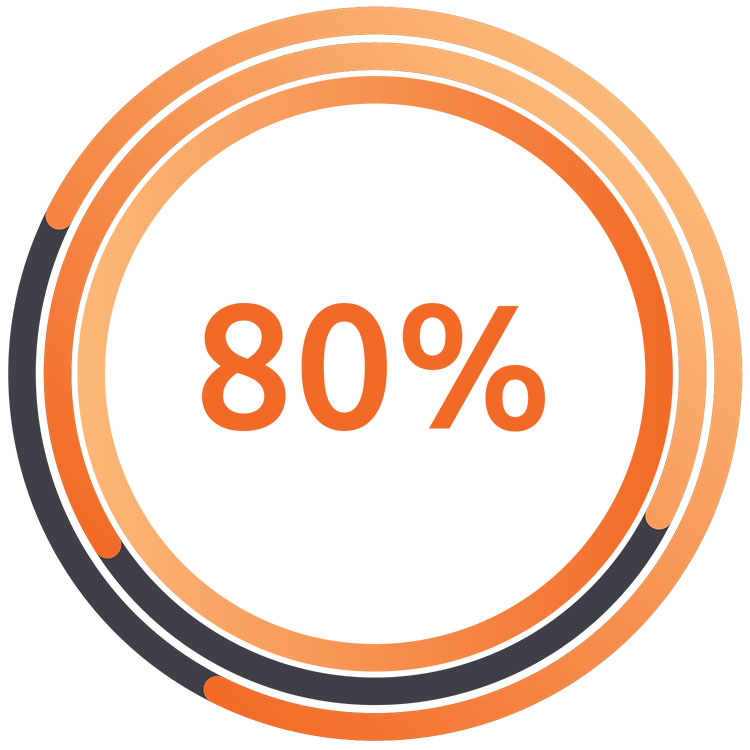
Non-approved SaaS usage: Shadow it.
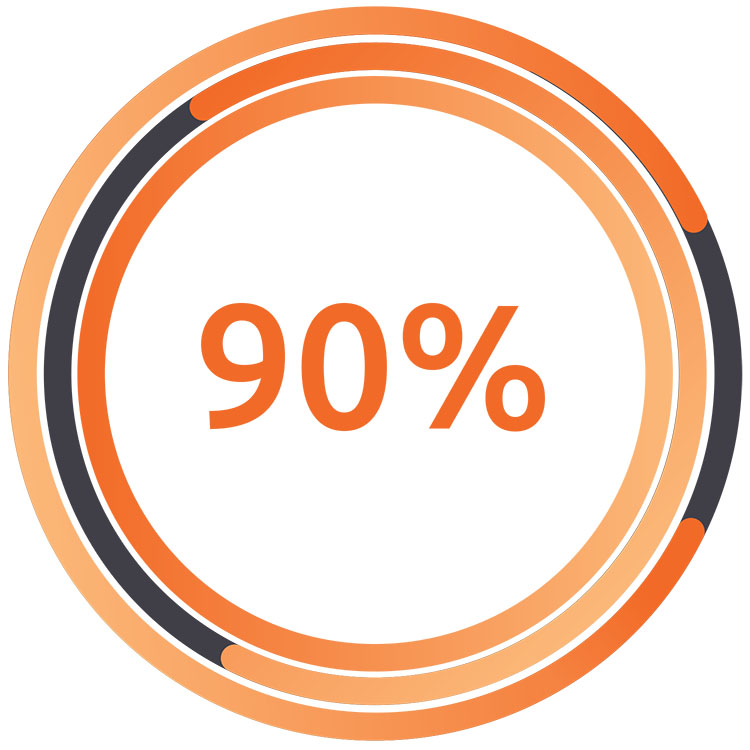
Data leakage: 90% caused by user mistakes.
Key Attack Zone 3: Device
53 seconds
A laptop is stolen nearly every minute.
55,000
Average devices compromised by Ransomware every month in 2016.
5 x increase from 2015 with 4 x increase in Android base.
200,000
PC’s attacked by WannaCrypt (ransomware) across 150 countries.
USD 1 Billion
Average earning of a hacker from Ransomware (FBI guesstimate).
Combat these threats with Intelligent Security
4 key areas to consider:




Secure the front door
Protection from identity driven data breaches, email attacks and attacks targeting operating systems.
Secure content
Protect content: At the time of creation, in transit and during consumption.
Secure devices
Workplace issued or BYOD devices.
Great employee experience
Productivity without compromise.
Microsoft 365 offers intelligent security across critical end-points to help ensure security, privacy, and compliance.
Microsoft 365 brings together Office 365, Windows 10 and Enterprise Mobility and Security. It’s a complete, intelligent solution that empowers everyone to be creative and work together securely.
Thwart advanced threats and protect identity, apps, data and devices;
- Protect, detect and respond to malware and data breaches
- Comprehensive, integrated solution with built-in security capabilities from end-to-end
- Provides a productive end-user experience with familiar tools and environment.
Our Partners
To support the nonprofit sector in Australia to tackle the spike in cyber attacks, Microsoft Tech for Social Impact Partner illuminance Solutions is working with Canadian cyber security firm Terranova Security to bring its globally recognised training courses to assist nonprofits in Australia, and has also partnered with the WA AustCyber Innovation Hub. The Cyber Security solution led by illuminance Solutions will allow nonprofits to access cyber security expertise while their staff are trained by international experts while Microsoft technologies are implemented to fit each nonprofit’s needs and requirements.
illuminance Solutions is a Microsoft Gold Partner and a 2019 Microsoft Global Partner of the Year: Partner for Social Impact.







